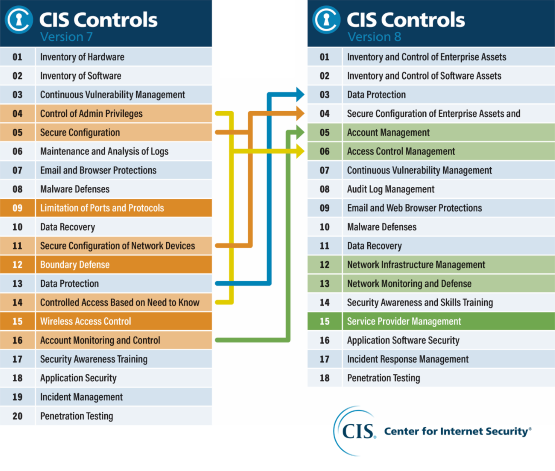
In May 2021, the Center for Internet Security (CIS) launched an update of the CIS 20 controls, which were enhanced to keep pace with modern technology (systems and software), increased threat landscape and the home workplace.
CIS 18 is the latest version of best practice recommondations for protection agains cyber threats from Center for Internet Security. The security controls bring together a number of security measures companies should apply depending on their profile. The CIS controls consist of 18 tangible controls that are measurable and with direct recommendations on how to implement them, focusing on vulnerability and threat.
The latest version includes cloud and mobile technologies, with a new control for “Service Provider Management” that provides guidance on how companies can manage their cloud services.
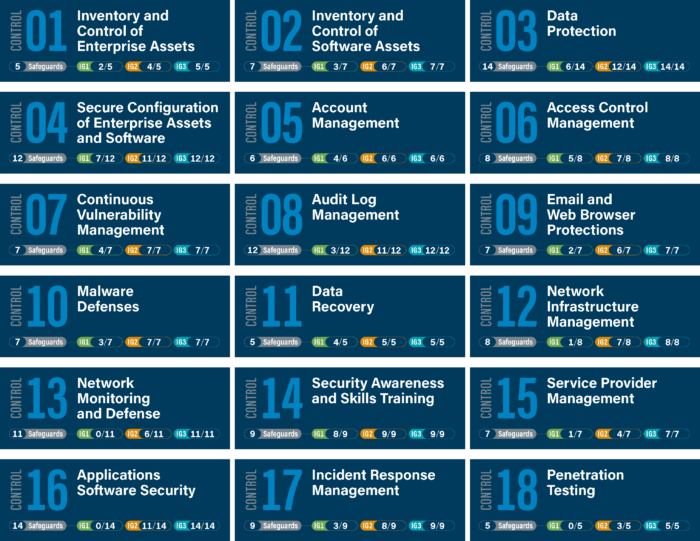
Efforts to streamline controls and organise them by activity resulted in fewer controls and fewer safeguards (formerly sub-controls). There are now 18 controls and 153 safeguards across three Implementation Groups (IGs).
IG1 = Basic cyber hygiene
CIS Controls v8 officially defines IG1 as basic “cyber hygiene” and represents a new minimum standard of information security for all companies. IG1 (56 Safeguards) is a basic set of cyber defence security measures that every company should apply to protect itself against the most common attacks. IG2 (74 additional Safeguards) and IG3 (23 additional Safeguards) build on previous IGs.
In 2021, the Verizon Data Breach Investigations Report (DBIR) issued a publication identifying a core set of controls that every company should implement, regardless of size and budget:
– Control 4: Secure configuration of corporate assets and software
– Control 5: Account management
– Control 6: Access control management
– Control 14: Safety awareness and skills training
How to approach the task?
I-Trust has extensive experience in helping organisations with security measures. The enablor platform has created a standardised approach to CIS controls, alongside a roadmap for a continuous approach to cybersecurity and IT security work. The platform provides the organisation with a central cybersecurity hub, replacing excel sheets with automated reporting, benchmarking and history capabilities, as well as a wide range of options that provide a clear picture of the organisation’s status and gaps.
The CIS controls are carried out on the I-Trust platform, enablor, with the following functionality available:
- Status – on all cyber security initiatives in the organization
- Recommendations – based on the extensive documentation and guidance in CIS 18
- Overview – of activities, evaluations and follow-ups
- Administration – of controls and units
- Activity Center – one place for gathering tasks, follow-ups, and repetitions
- History and benchmark – status development and comparison with reference groups
- Reporting – reports to management and line managers
- Module for analysis – BI analysis on status

