Cyber Security
We live in a digitalized age and a society where both private companies and public authorities offer a lot of digital solutions for customers and citizens. The digital possibilities provide great value, many tasks can be solved quickly and easily online. But digitization also brings challenges, as cybercriminals are constantly looking for new opportunities to cheat and deceive.
Rikke Hougaard Zeberg, Head of the Agency for Digital Government (Denmark)
I-Trust's cyber security program is based on CIS 18 controls
CIS 18 is the latest version of measures for improving companies’ cyber security. The framework consists of 18 focus areas covering a whole array of precautionary measures organizations should have in place to be protected from cyber threats. The use of the controls can be divided into three groups according to the type and size of the organization.
The controls are mapped to the current cyber threats and thus give the company a picture of its exposure.
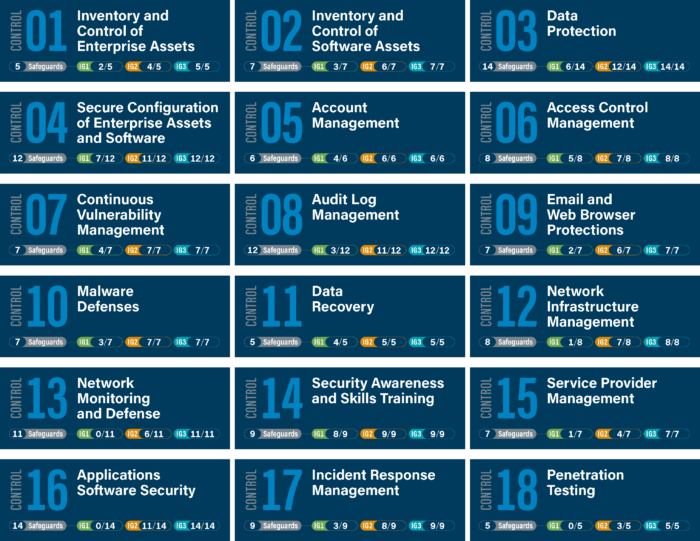
CIS 18 is structured pragmatically, and forms the basis of efforts in practice:
– Cyber security is made measurable
– Facilitates prioritized initiatives
– Method that forms the basis for fulfilling best practice.
Thomas Lund-Sørensen, Head of the Center for Cyber Security (Denmark)
Benefits:
- Detailed clarification of the company’s vulnerabilities and cyber security
- Measuring the company’s possibilities of working with cyber security
- Threat assessment of whether the cyber security controls uncover the relevant threats
- Specific recommendations to reduce vulnerability
Excel sheet or SaaS Platform?
In the platform enablor, I-Trust has a standardized method for companies’ work with the CIS controls. The platform provides the organization with a central cyber security hub, replacing excel sheets with automated reporting, benchmarking and history capabilities, as well as a wide range of options that provide a clear picture of the organization’s status and gaps.
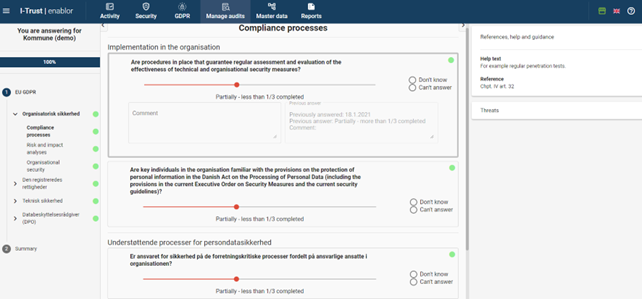
The CIS controls are carried out on the I-Trust platform, enablor, with the following functionality available:
- Status – on all cyber security initiatives in the organization
- Recommendations – based on the extensive documentation and guidance in CIS 18
- Overview – of activities, evaluations and follow-ups
- Administration – of controls and units
- Activity Center – one place for gathering tasks, follow-ups, and repetitions
- History – status development and historical frame of reference
- Benchmark – comparison with results from other organizations
- Reports – reports to management and functional managers
- Analysis module – BI analyses of status
Example: One-Pager status report
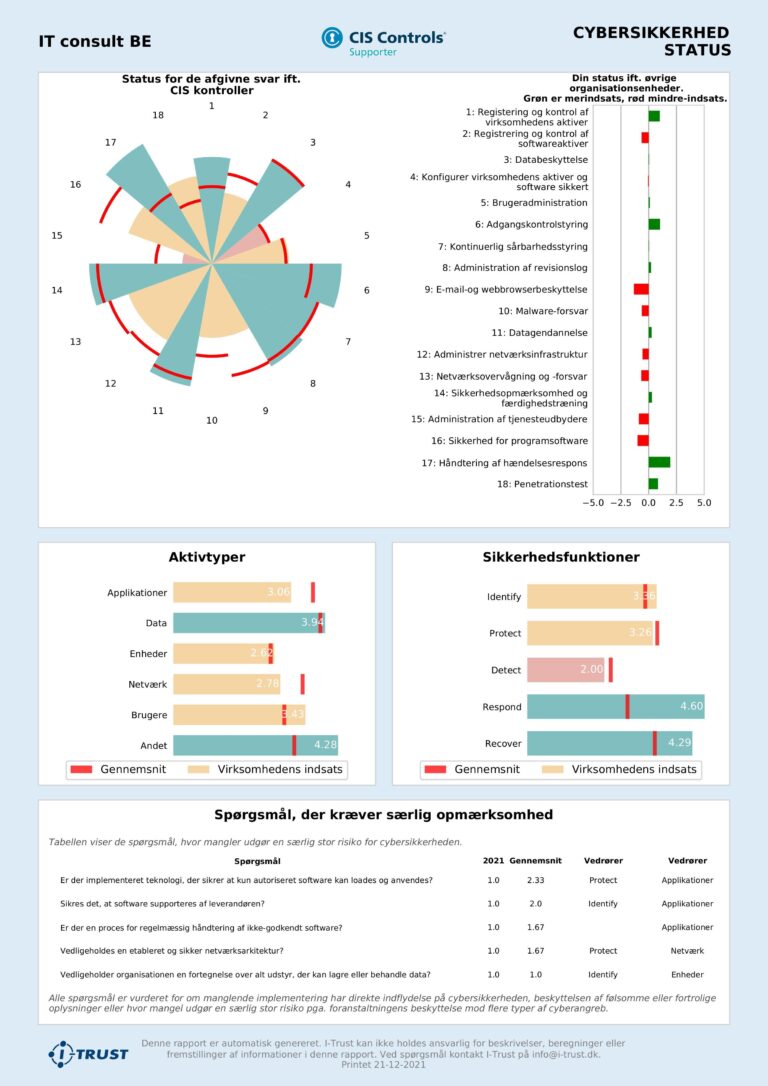
Since 2004, I-Trust has worked with assessments of companies’ compliance and digitalization. The enablor platform is a result of the collected experiences and is developed for efficiently collecting and processing data. I-Trust is an official CIS Controls Supporter, giving our partners access to the controls, as well as a wide range of best practice recommendations.
Book a no-obligation meeting with one of our consultants, and get a security overview of your organization’s overall digital activities with an I-Trust Security Assessment.
Are you already using CIS controls in your organization or on behalf of clients? Contact us and let’s find out if we should replace your excel sheets with one unified platform.

